To learn more about data security in the workplace, checkout this infographic compiled by the University of Alabama at Birmingham’s Online Master of Science in Management Information Systems program.
Uncover and Mitigate Third-Party Risks
- GRC
- 02 June 17

Introduction
Third parties have become an integral part of any business operation. However, the threats and issues arising from third-party engagements require enterprises to gain an in-depth understanding of their entire global third-party ecosystem. Failing to curb third-party risks can lead to severe reputational damage and loss of stakeholder and customer trust, but assessing third parties can be resource intensive. On the other hand, establishing a robust and automated program to continuously monitor and assess third parties enables organizations to detect and alleviate risks stemming from non-compliance, unethical practices, financial risks including supplier bankruptcy or business disruption, exposure to Tier 2 suppliers, legal issues, and access to confidential data.
By leveraging leading financial health analytics providers for a deep analysis of the financial viability of third parties, and by adopting robust technology, organizations can simplify the process of third-party risk management and catch early signs of risk exposure.
Recently, MetricStream hosted a webinar on the topic, where experts James H. Gellert, Chairman & CEO at RapidRatings, and Swapnil Srivastav, Manager, Marketing at MetricStream, provided some key insights into the best practices that can help organizations effectively identify and mitigate third-party risks.
In the course of the webinar, several interesting audience questions were addressed. I have highlighted some of the insightful ones below:
Q1: Do you have different metrics or methodologies to understand the financial health of private companies vs. public companies?
James: “To understand a company’s financial health, RapidRatings uses a proprietary quantitative system that looks directly at the company’s financial statements to determine its short-term financial health (12 months ahead) and the long-term core health (3 years ahead). So, whether you’re looking at private companies or public companies, we’re evaluating them all through the same methodology. That is really the key because for many organizations, private companies make up over 70% of their third-party relationships, meaning they need a metric to evaluate their entire third-party ecosystem consistently. Given that our system requires financial statements as its only input for computing the financial health, we’re able to compare companies on an apples-to-apples basis, regardless of ownership, company size, industry, or geography. So, part of the premise is to be able to provide a single common language that is repeated every time we are re-rating a company, whether quarterly or annually, and to give back a consistent measure irrespective of whether a company is public or private.”
Q2: How do your Financial Health Ratings account for companies that operate in different industries?
James: “The financial profile of a technology start-up will look very different than that of an auto manufacturer or a retail company. Depending on the industry, there are different triggers that will affect a company’s growth or long-term and short-term risks in different ways, and our system accounts for these nuances for 24 individual industry models. RapidRatings applies 73 different financial and operating ratios to over 25 elements of a company’s financial statement. This data that is used to calibrate the system is about 9 million company years of data. So, a significant amount of econometric analysis is needed to be able to look at the companies in different industries, and to be able to provide a financial health rating that accounts for the nuances and idiosyncrasies in each of those industries, regardless of whether we’re dealing with a software company or a logistics company. That’s again very much part of the premise that in order for people to be able to use financial health, and to use it in as robust a way as possible, it is important to have a common signal for each risk management process in an individual company that is replicable and scalable – it’s very much a part of the thesis behind the Financial Health System™ that we have.”
Q3: What happens when a private company doesn’t want to release their financials to you?
James: “Yes, there are certainly some groups that are reluctant, and often, the fact that they don’t want to disclose their financials is, in itself, valuable information. We have lots of clients who will take different actions on a company that does not disclose information, and chooses to opt out of this program. Some of the actions are to discontinue the business, or to not award future business, or to reduce business and to be more hedged in in terms of the long-term and short-term nature of association with such a vendor. Organizations basically begin to reduce the potential risks by taking action on the very fact that a third-party does not disclose financial information.”
For more details about Rapid Rating and their offerings, click here.
Principles of an Effective Cybersecurity Strategy
- IT Risk & Cyber Risk
- 28 April 17

Managing Cybersecurity Risks
A number of trends contribute to today’s reality in which businesses can no longer treat cybersecurity as an afterthought. These include a rapid increase in the number of internet connected devices, an increased dependency on third party applications, self-provisioning as a result of bring-your-own-device and public cloud. Add to these, unprecedented levels of smart phone and mobile device adoption and we can see that the cybersecurity ‘attack surface’ has increased massively.
According to MetricStream’s, ‘The State of Cyber Security in the Financial Services Industry’ report, around 66 percent of financial services institutions have faced at least one cyber-attack in the last 12 months. The cost of this, which can be catastrophic, can include regulatory penalties, eroded share prices, a loss of customer confidence and reputational damage. It can even result in a complete shutdown of the business.”
It is clear therefore, that organizations need to constantly evolve their security strategies and tactics to safeguard data, systems and operations against ever-evolving security risks.
In today’s cloud era, an effective strategy should leverage industry-standard cybersecurity frameworks and unified threat management systems. A sole reliance on traditional approaches and tools, such as firewalls and security solutions, may now leave networks exposed.
Companies attracted by the cost, flexibility and adaptability of cloud still have concerns over how secure it is. According to Crowd Research Partners’ 2016 Cloud Security Spotlight Report, security concerns top the list of barriers to cloud adoption and one in three organizations say external sharing of sensitive information is the biggest security threat.
Understanding the Cyber Landscape
The constant threat of cyber-attacks hangs over all businesses. So prevalent are security breaches that over half (54 percent) of cybersecurity professionals anticipate a successful cyber-attack on their organization in the next twelve months, while Ponemon tells us there is a 26 percent likelihood that a material data breach involving 10,000 lost or stolen records will occur in the next 24 months.
The explosive growth in digital transactions, together with the increased volume of personal and sensitive information now stored digitally has raised the potential for targeted attacks. The emergence of cybersecurity threats can be broadly attributed to:
- Consumerization resulting in a loss of data control and device usage beyond the traditional data center
- Collaboration that means highly sensitive data is now shared across channels and platforms
- Innovation, and with it the lack of clear understanding of the risks and threats due to cloud, social media, virtualization, mobile and shared services.
It is a challenge to keep pace with technological change and to adapt to new ways of protecting data from internal and external threats. Not surprisingly therefore, cybersecurity is one of the top priorities for regulators during supervisory reviews.
Add to this the complexity of maintaining compliance with evolving regulations, such as the EU’s General Data Protection Regulation (GDPR), Federal Information Security Management Act (FISMA), Gramm-Leach-Bliley Act and the Homeland Security Act and a significant effort has to be put into assessing current policies and practices to ensure compliance.
Principles of an Effective Cybersecurity Strategy
An effective cybersecurity strategy should be sufficiently flexible to cope with the evolving threat landscape and should:
- Include the implementation of security policies
- Incorporate security assessment models such as the Open Web Application Security Project (OWASP), the Software Assurance Maturity Model (SAMM) and other industry standard frameworks
- Monitor for early warnings, continually gathering threat intelligence accordingly
- Include a rapid response plan including crisis communications, so that the business is prepared to minimize material impact should a cyber-attack occur.
A cybersecurity framework is a good starting point for enterprises to define, adopt and refine the critical infrastructure. It helps organizations to assess current capabilities and draft a prioritized roadmap towards improved cybersecurity practices.
Frameworks provide a toolkit to assess security measures against industry standard best practices and compliance requirements. The Federal Financial Institutions Examination Council (FFIEC), National Institute of Standards and Technology (NIST) and other regulatory bodies have all released specific frameworks and tools to strengthen cybersecurity policies.
Enterprises today allocate considerable budget and resource to establish security policies and adopt industry frameworks. However, with threats becoming more sophisticated, it is extremely important for organizations to invest in threat intelligence systems and better business continuity, disaster recovery and redundancy mechanisms.
What Cybersecurity Means in a Cloud Era
Cloud abuse is one of the top cybersecurity threats. The recent spear phishing campaign on Dropbox’s cloud storage, where the attackers were able to carry out their activity while hiding as legitimate users shows that attackers continually adapt new technologies as well as vulnerabilities to further their ends.
Alarmingly, as per the 2016 Cloud Security Spotlight Report, a huge majority (84 percent) of cybersecurity professionals are dissatisfied with traditional security tools when applied to cloud infrastructure. The report also states that unauthorized access or improper access controls is the single biggest threat to cloud security, followed by hijacking of accounts (44 percent) and insecure interfaces/APIs.
Organizations need secure cloud to preserve the integrity of systems and operations and to protect their data, and for this they must work collaboratively on risk assessment and security planning with cloud service providers. Clarity and rigor is required around security protocols including access and data separation as well as roles and responsibilities around compliance and assurance over business continuity.
Is Cloud Enabled Cybersecurity the Way Forward?
PwC’s Global State of Information Security Survey 2016 highlights the importance of using cloud-based monitoring and analysis technologies and adopting new safeguards for digital business models. Cloud-based threat management systems allow organizations to rapidly identify and analyze a threat in order to take action.
The future lies in harnessing the power of cloud to improve cybersecurity for organizations. This includes using cloud to create highly secure platforms which can be used to block any tools and procedures used by the attackers.
The original article was published by Cloud Tweaks. You can view it here.
Components Of An Effective Third-Party Due Diligence Program
- IT Risk & Cyber Risk
- 13 April 17

Introduction
Third-party intermediates such as distributors, resellers, agents, service providers, or business consultants are contracted to rapidly create a presence in or access to new or emerging markets. They can work as the first foothold in opening a commercial presence, both domestic and internationally. Also, they can provide insights of the local business environment and their relationships as a business partners. While third parties are retained to operate on the organization´s behalf, their business activities are not always as transparent or controllable. It increases the exposure to bribery and corruption risks. Intermediaries include not only those used in the sales channel, but also as part of a business operations and strategy.
A third-party due diligence program (KY3P) allows reducing the risk of improper payments and fraud. In addition, regulations such as the FCPA and the UK anti-bribery act, settlement agreements, enforcement actions, ISO standards and best practices, require a third-party due diligence program as part of the corporate ethics and compliance program.
The following components are part of an effective program:
Risk-Based Approach: the first step in the program is to perform a risk assessment of third parties, usually classified into low, medium and high. These risk tiers define how deep the investigation should be performed. For instance, the risk approach should identify key factors such as interaction with government customers and other politically exposed persons, unclear ownership and control of the third party, expected purchasing volume, perceived country corruption risks, exposition to regulatory enforcement, type of business relationship, and level of confidentiality and dependency.
Consistency: automating the control activities and developing templates for selecting third parties will help drive consistency across the organization. A robust procedure will be critical for organizations with decentralized compliance departments or lacking of integrated GRC software. The third-party base should be centralized to have all the information visible and controlled. Training on the anti-bribery policy and trade compliance should also be given on specific criteria to all agents and intermediaries.
Management involvement: compliance and commercial executives should be involved during the third-party due diligence process to identify other risks or action plans. Workflows should be able to escalate approvals in the decision-taking process, and the remediation plans, especially when some risks cannot be avoided. The management involvement includes the compliance and legal departments, and also sales, finance, exporting and data privacy experts. The due diligence program and the anti-bribery commitments should be well communicated, internally and externally, by the top management.
Efficient, reliable and scalable: controls and validations should be reasonable to address the risks in a well-thought-out process. Contracting considerations with its third-party partners should address key risk by selecting specific acceptance procedures to each case. For instance, specific procedures include due diligence questionnaires, business justification memorandums, certification, targeted training, extended background checks including financial checks, in- depth review of sanctions and watch lists on different jurisdictions, and on-site visits and interviews
Comprehensive: Both internal and external information should be used during the due diligence. It is important to get risk information from outside the organization, such as sanction lists, financial and political exposed person lists, credit ratings, and adverse media.
Independence: conflicts of interest should be avoided during the investigation and action plans to assure the objectivity in the selection process. Due diligence procedures should be independently performed and approved from the requestor. The acceptance of agents should be removed from the business operations.
Continuous monitoring: changes in the risk profile on agents should be proactively monitored to adjust the screened controls. Automated database searches should be systematically performed on the third-party base.
Which best practices have you identified in implementing a third-party due diligence?
The original blog appeared here.
What Is Important? Cyber and Continuity Risk
- IT Risk & Cyber Risk
- 05 April 17

Introduction
New risks are emerging every day in the realm of Cybersecurity, and many organizations are moving quickly to address these risks: developing documentation, procedures, and processes. However, this is often without regard for Cybersecurity best practices. To ensure sustainability, organizations must develop cyber policies, plans, and procedures and put effective controls in place. If these controls are already in place, they should be evaluated frequently to ensure that they address these emerging risks.
It is essential for every organization to review and update their security procedures and policies in order to prepare for emerging business and IT risks. Having a standard and consistent monitoring and incident response program is becoming more and more critical, as attacks occur more often and more viciously, targeting organizations across sizes and industries. In addition, the organizations need to constantly upgrade their security awareness and training programs to educate the employees and other stakeholders about new technology advances and techniques and tools available to prevent cyber attacks. Digital enterprises today need to tailor standard cyber risk methodologies, based on best practices, such as ISO 27005 to fit their organization.
In the event of an attack, to ensure that critical business processes aren’t brought to a standstill, disaster recovery (DR) and business continuity planning (BCP) must be incorporated into the overall cyber-security program. A cyber incident affects both business and technology, thereby requiring disaster recovery and business continuity plans to be invoked and operationalized.
Cyber Security Policies, Plans, Procedures and Controls
Cybersecurity policies, plans, and procedures, though connected, play different and distinct roles. A policy is the highest-level document that expresses what an organization, group, or division will and will not perform in terms of managing information and managing the associated risks. A plan is a document that outlines a clear path to accomplishing the policy’s goals. A procedure is specific step-by-step directions to the operator on how to effectively execute a particular task.
Controls are put in place to guard a system against loss or damage. For example, implementing a system of identification and authentication controls ensures that only authorized users and system components can access vital data. Though controls may vary, the end objective is to always mitigate or reduce a risk in some form.
Security Personnel, Physical and Environmental Security
According to the FBI’s Cyber Crimes Division, the majority of all data theft and computer-related crime happens via internal sources. Therefore, implementing personnel security measures, appropriate to the type of business and data to protect, is crucial. Executing potential safeguards, like performing extensive background checks on new employees, separating duties, and administering the right controls such as instant revocation of credentials after dismissal of an employee, all combine to help mitigate risk posed by internal personnel. Physical and environmental security are equally important to protecting an organization from attacks.
Awareness and Training
The most vulnerable aspect of a system is undoubtedly the human element. Users need to be trained on how to protect the system from unauthorized access to valuable and confidential data. Also, users that have other important information and knowledge serve as one of the biggest vulnerabilities for a cyber intruder. The training should include both technology and behavioral aspects to ensure that users are not divulging critical information over phone calls or emails without sufficient verification. Security training and constant reinforcement via ongoing awareness information sessions reduce the risks affiliated with the human element of a security strategy.
Monitoring and Incident Response
During an emergency event or situation that leads to system failure, a detected or active intrusion, or a virus attack, following a standard protocol and response team is important for timely and effective incident response. It limits the extent of damage an attack can have on the organization.
Business continuity planning and plan exercising are important parts of ensuring a coordinated and standard incident response. It significantly limits the damage as well as improves recovery time.
Disaster Recovery and Business Continuity Planning
IT systems are considered vulnerable to a range of adverse events with the potential of seriously impacting standard business operations, possibly compromising confidential data or integrity and availability of information. Even though proper preparation and effective planning are vital mitigation strategies, it is impossible to completely eliminate the risks and the potential damage posed. Due to this situation, organizations need not have any illusions about the potential threats.
Companies should take utmost care when planning precise steps to take during the event of a system disruption, no matter the magnitude. By ensuring a climate of constant testing and adjustment, implementing effective plans prior to any disruption can mitigate the potential damage and can significantly lower the potential loss of productivity, revenue, and information.
Configuration Management
Without a clearly defined process that carefully accounts for policy mandates, security concerns, business impact, authorization, and oversight, changes to configuration seriously may affect the stability and security of a system. As a result, organizations need to follow standard configuration management processes.
A configuration management process makes sure that network and system updates decrease the chances of penetration via malicious code. It also works to reduce the likelihood of human error.
Furthermore, adding to the security benefits, following a specific and formal change, management process derives more business benefits. These added benefits include having a duplicable process for recreating a product, the capability of efficiently reusing components of a project or product, and important safeguards against loss of intellectual capital should any loss of key personnel occur.
Cyber Risk Methodologies
Cyber risk methodologies normally entail a variety of processes to promptly detect and assess risk to a system or group of systems, providing a duplicable technique to conduct and administer risk management. Most obvious to all methodologies are implementing the necessary resources to execute risk assessments, performing system testing including observation, data analysis, and electronic testing (e.g., vulnerability scanning, penetration testing), and lastly, establishing a way to track and monitor system vulnerabilities and mitigation activities (e.g., plan of action).
Senior management needs to standardize and endorse the risk identification methodology to ensure effective results and consistency across the entire organization‘s critical IT functions.
Summary
Comparison of current cyber security activities with the desired level of preparedness enables the designated staff to identify weak links properly and to deploy the necessary enhancements that can be accounted for to justify the investment budget. Establishing and enhancing cyber security capabilities that are fully integrated into ongoing state of preparedness and efforts help build a solid bedrock to drive collaboration and coordination from across functions and through all levels of the organization. As there is more technology integrated into our nation’s prevention protection, response, and recovery activities, cybersecurity will continue play a crucial role.
The blog content is contributed by Michael Redmond & Vibhav Agarwal. The original blog was published by Disaster Recovery Journal. Click here to view it.
Promoting Data Security in the Workplace
- Compliance Management
- 14 March 17

No matter the workplace, data security is often a top concern for management professionals. Security breaches can end up threatening the livelihood of employees and entire companies alike, depending on how severe they are. There are solutions available to
Employees and General Information Security
Over eighty percent of companies say that their biggest security threat is end user carelessness. Seventy five percent of companies also believe that employee negligence is their greatest security threat. Three percent of all United States full time employees admitted to using the same collection of passwords for their online needs. A third of this percentage even admitted to using less than five different passwords to access anywhere between twenty five to fifty websites, some of which were business and professional locations. Over thirty three percent of US companies do not have a security plan for internal security risks, which means personal responsibility is the largest deterrent in a vast majority of these incidents.
Top Mistakes
Many mistakes committed by employees are entirely avoidable. Things such as sharing passwords with others and leaving their computers unattended outside the workplace all contribute to security problems. Employees are strongly encouraged to use different passwords for different websites, and to change them frequently. Additionally, it is important to delete data when it is no longer being used on the computer, as well as avoid connecting personal devices to company networks and databases.
Largest Threats to Information Security
Senior managers are as much a culprit of problematic behavior as their employees. Over fifty eight percent of senior managers have accidentally sent crucial and private company information to the wrong people. Fifty one percent of all senior managers have also taken private files from the company with them after they left the job. Business owners may end up compromising their own company’s security as well. Over eighty seven percent of all business owners regularly upload files from work to a personal cloud or storage network. Sixty three percent of those same business owners also use the same passwords to log into different systems in both business and personal affairs.
Tips on Promoting Security
There are many solutions that can be taken to help keep the workplace safe. One of the first of these is to implement a strict, written set of security guidelines. Enforcing physical restrictions to personal data is also recommended. Destroying older data in a more timely fashion can also help resolve many security risks. Generally raising security awareness in the workplace by training and educating employees in proper and improper behavior can be a good idea. All business owners and leaders are strongly encouraged to become more vocal about security in the workplace.
Employees and Specialized Training
Proper information and security training on a professional level can also help reduce the frequency and severity of security breaches. Over thirty seven percent of employees had received mobile security training, while over forty percent of employees had received information sharing training. Increasing this number can help spread security awareness in the workplace on a much more efficient level, and businesses are encouraged to introduce some type of professional training program.
Current Bring Your Own Device Practices
Fortunately, while there is room for improvement in many companies, management professionals are also looking into ways to help improve Bring Your Own Device standards and practices. Over forty percent of companies currently consider mobile device insecurities to be a large security concern. Fifteen percent of employees believe that they have minimal, or practically no, responsibility to safeguard the personal data stored on their devices. This type of thinking is what encourages security risks to occur in the first place. As a result, there is going to be an expected increase in security strategies of upwards of sixty four percent for employees concerning the use of their personal devices over the next twelve months.
Information Security Recommendations
Numerous security recommendations are already being considered by many companies and many businesses are planning on introducing more data leakage protection to help control what data mobile employees will be able to send through Bring Your Own Device practices. This can help prevent the transfer of regulated data through unsecured apps. These plans can also help prevent employees from accessing data on unsecured devices, or transferring unsecured data on their own devices. Future demands will also require owned devices to have a password necessary in order to access the stored data. Many training programs are also going to be planned as well, which will inform employees of the necessity of adhering to, and enforcing, data security regulations.
The following blog post was originally posted here and is reposted with the authors permission.
5 Recommendations For Effective Governance, Risk And Compliance Management
- GRC
- 28 February 17

Introduction
Cloud adoption continues to grow, which is evident from the fact that annual 2016 revenues for cloud vendors were “within touching distance” of $150 billion. Gartner also predicts that, a corporate ‘no-cloud’ policy will be as rare by 2020 as a ‘no-Internet’ policy is today. However, a ‘’cloud-ready’ security and compliance program is the need of the hour, to manage the risks and the complexities due to cloud adoption. This will enable organizations to face cloud challenges which, according to RightScale’s 2016 State of the Cloud Report include compliance with regulations, a lack of resources and expertise, governance and control and security. Although a challenge mainstay, confidence in cloud security is nonetheless rising; SkyHigh Networks points out that 65 percent of IT leaders think the cloud is as secure, or more secure, than on-premises software.
To maximize the benefits of cloud deployments while mitigating the risks, companies need to prioritize a cohesive approach to governance, risk management and compliance (GRC). A cloud governance framework can automate cloud security, risk, and compliance workflows, enable stakeholder reporting and visibility, and ensure best practices and standards for cloud compliance.
With that in mind, here are five recommendations for ensuring a proper governance, risk and compliance framework for cloud assets and operations:
1. Improve cloud asset / service visibility
An essential first step is to understand the scope of cloud services in use within the organization and gain visibility into the whole cloud environment. IT and infrastructure managers need to have a complete picture of the processes running on cloud deployments, the underlying assets and their ownership within the organization both from an IT and business standpoint. While they may seem intuitive, alarmingly, the 1H 2016 Shadow Data Report states that organizations use 841 cloud apps on average – an astonishing 20 times more than they thought they did. Organizations also need a well-defined policy to deploy, manage and run the cloud applications and categorize the sensitivity of the data held to ensure that requisite controls are in place to manage the data.
2. Assess the cloud service provider (CSP) continuously
Businesses always have the thought of losing control on application and infrastructure while deploying an application on the cloud. Assessing and creating a working relationship with the cloud provider based on a mutually agreed framework is very important. The organizations must select a cloud provider who can demonstrate validation of controls including network security, physical datacenter security as well as a standard audit framework conforming to applicable regulatory standards.
Gartner recommends that organizations need to address several key issues when selecting a cloud hosting provider, which include access privileges, regulatory compliance, data provenance, data segregation, data recovery and business continuity.
To gain a complete understanding of the CSP environment, organizations should also ensure that there is no ‘insufficient due diligence’, which Cloud Security Alliance (CSA) rates as one of the ‘notorious nine cloud computing top threats, and establish a due-diligence framework to monitor the cloud service provider performance on a continuous basis.
3. Assign business ownership and accountability for critical cloud assets and services
Organizations should understand the importance for an effective governance function within the cloud environment. The cloud assets, cloud services, business objectives, business processes, policies must be documented, along with their operational relationships. These processes and policies must be accountable, clearly assigned and consistently understood throughout the business.
Also, it is of utmost importance to establish accountability when customer information is intertwined with that of the cloud service provider. This includes logical separation of your data sets from those of the other customers / users, defining SLAs on both sides and categorizing the services consumed.
4. Know the cloud threat landscape and evaluate risks
Inevitably, there are risks with cloud environments as there are with all storage and retrieval systems, both electronic and manual. Businesses must understand the cloud threat landscape, effectively evaluate and mitigate risks and protect themselves and their interested parties from exposure.
The likelihood of threats rarely lessens, but threats do change in nature and for this reason companies should be continually alert and abreast of latest developments. SkyHigh Networks revealed, in its Q4 2016 Cloud Adoption and Risk Report that the average company experiences over 23 cloud-related security incidents each month. Yet, despite this, a different study – the 2016 Global Cloud Data Security Study from Gemalto and the Ponemon Institute – discovered that 54 percent of respondents didn’t agree that their companies have a proactive approach to managing security and complying with privacy / data protection regulations for the cloud. Therefore, it is imperative that organizations prepare for security threats to the cloud before becoming a victim.
5. Leverage standard risk / control frameworks to assess compliance
Businesses should assess cloud compliance with regard to security, privacy practices and policies. Among the most well-known risk and control frameworks are best practices is the Cloud Security Alliance (CSA)’s GRC stack, which provides a toolkit to assess private and public clouds against industry standard best practices and compliance requirements.
Others include the CSA’s ‘Treacherous Twelve’ Cloud Computing Top Threats, ISACA’s Cybersecurity Threats and Controls, the National Institute for Standards and Technology (NIST)’s Framework for Improving Critical Infrastructure Cybersecurity, ISO/IEC 27017, ISO/IEC 27018 and the Center for Internet Security (CIS)’s Critical Security Controls.
Leveraging industry standards provides a level of assurance that best practices are followed both by the organization and by cloud service providers.
Businesses can achieve enhanced information security, compliance and risk management as well as reliability, operational control and transparency with effective implementation and extension of the GRC framework to their cloud assets and operations. Adhering to best practices and standards will deliver informed decision-making and ongoing management, placing the business in a better position to reduce risk and realize the benefits of the cloud in enhancing business performance.
The original article was published via Cloud Tweaks here.
5 Simple Tips To Make Strong And Robust Business Continuity Plans
- IT Risk & Cyber Risk
- 23 November 16

Business Continuity Plans
Today’s organizations need comprehensive and robust business continuity planning for swift and effective action in case of a disaster or crisis. As the trade and supply chain have gone global, businesses today expect crisis response to be in seconds, not in hours, to ensure that the ripple impact is minimized. As organizations go digital, an IT failure can cripple the whole supply chain and business operations, causing extreme losses within hours and requiring countless hours to recover from the them. Plans to mitigate IT failures are also affected by the complexity of today’s IT infrastructure. As applications and systems are added based on business and market requirements, newer technologies and infrastructure pose new challenges.
Most businesses leverage cloud based platforms for their enterprise needs at least partially. The cloud helps businesses minimize costs and maximize efficiency; made for speed and convenience, it can scale up and down as needs demand and bring flexibility to business operations. However, the added overhead of managing cloud data centers, planning and performing test exercises across multiple locations and vendors as well as managing a crisis recovery, requires that organizations pay critical attention to their cloud solutions in combination with legacy infrastructure.
Today, an effective business continuity plan requires dynamic collection of information across the extended organization in a continuous manner. Organizations need to overcome the traditional fragmented approach to business continuity and formulate the business continuity strategy that adheres to the following five-point agenda:
1. Champion Business Continuity at the Highest Level
With senior management sponsorship, the business continuity plan will occupy its rightful position, high up in business priorities. This is important for sufficient budget, resourcing and training to be assigned to it. Senior leaders must set the tone at the top by insisting on robust crisis planning and regular reviews as a standard practice rather than a mere formality.
In August, Delta suffered a major IT outage that resulted in a $100 million loss in revenues for the airline. The impact was far-reaching, affecting check-in systems, flight information screens, the airline’s website and smartphone apps. The disruption to customers was extensive as well.
This is just one example of many; unfortunately, downtime of one type or another is a common situation in business. According to the Continuity Insights and KPMG, Global BCM 2016 report, 39 percent of global organizations have estimated the cost of business disruption to be $100,000 or less and 27 percent have estimated business disruptions ranging from $100,000 to $5 million or more in the last 12 months . This highlights the need for robust business continuity planning, championed at the highest level.
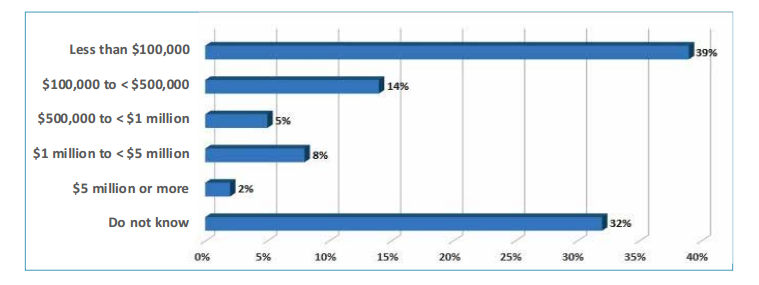
Types of Instances and Interruptions in Past Year

2. Review, Update and Test Regularly
The business continuity plan is a living document; it isn’t one to be created, filed and never looked at again. Risks evolve. Exercising the plans on a regularly scheduled basis will ensure businesses keep pace with the changing environment and understand what’s needed to protect critical infrastructure and preserve operations during a physical or virtual attack. Companies must learn from their own experience. Worryingly, according to Forrester and the Disaster Recovery Journal, 33 percent of businesses who had to invoke a business continuity plan, said one lesson learned from the experience was that the plan was out of date. Yet, 60 percent never carry out a full simulation of their business continuity plan for the entire organization; most walk through the plan as a document review.
It is of utmost importance that business continuity plans be reviewed by senior management and the planning team. Also, test results should be periodically evaluated and reported to the board, to assess the nature and scope of any changes to the organization’s business.
3. Include Partners, Suppliers and Third Parties
Companies don’t pay enough attention to the significant role of partners, suppliers and third parties in their business continuity. Deloitte found that over 94 percent of survey respondents had low to moderate confidence in the tools and technology used to manage third party risk and 88 percent felt the same about risk management processes. This, despite 87 percent having experienced disruption in the past three years that involved a third party.
Business continuity planning and disaster recovery has to be part of early third party discussions with responsibilities documented in service level agreements. Plans need to be aligned so that it is clear and easy to identify who does what, and where the handover points are when a plan is executed. The tools and systems used for collaboration must support transparency of information so that both parties are able to work from up to date information and take swift action in the event of a crisis.
4. Prioritize Ongoing Business Operations
The continuity plan should demonstrate that the business understands the priority level of its systems and that mitigating plans are in place to restore core operations as quickly as possible.
In the case of the Delta crisis, the outage was so extensive that it paralyzed business critical operations. The range of problems that can disrupt business – natural disasters, industrial action, cybercrime, IT failures, political or economic upheaval, suppliers ceasing to trade and so on – is so vast, and the systems and operations that can be impacted can be so wide that prioritization is a must.
A cloud-based option provides many benefits as an off-site back-up solution to ensure the efficacy of your continuity plan. However, as you develop your plan, ask yourself if a cloud-based option would increase the efficiency and cost-effectiveness of your plan and cover off essential considerations such as due diligence and service reliability with their provider. Another option is establishing a back-up plan that is independent of the cloud by leveraging personalized file backups, cross-device continuity solutions and communication software. The main aim is to get back faster and limit the amount of time that you’re spending without access to critical systems and information, by having a clearly defined continuity plan in place.
5. Define the Communications Plan Clearly
The business continuity plan has to be absolutely clear on how all stakeholders are going to be kept informed and how to enable upstream and downstream communication channels in times of crisis. Stakeholders include employees at all levels of the organization, such as suppliers, partners and customers.
The goal of the communications plan is to outline the channels and mechanisms for the sharing of information that will support efforts to resolve an issue at hand and limit the extent of its damage. How a company handles a crisis has an enormous impact on how they come out of the incident – people remember how the organization dealt and reacted to the issue and how convincing they were over the company’s efforts to make things right. For this reason, crisis management communications must be engaged at the earliest opportunity.
Service disruption is damaging to all businesses not only in terms of immediate revenue loss but also in the longer term brand and reputational impact. The business continuity plan is an essential, living document that aims to protect the ongoing sustainability of the business. Those that plan and execute well will see better performance in the long-run and be best-placed to weather the storms, whatever form they take.
The original article was published in Cloud Tweaks. You can view the article here.
Ensuring Resilient Cyber Safeguards in Cloud Applications
- IT Risk & Cyber Risk
- 12 October 16

Assessing Cloud Application Vendors from a Security Perspective
Enterprises of all structures and sizes across the globe have been adopting cloud for all needs – for computing, storage, databases, to hosting business applications. They are also proactively addressing cyber-security needs – both as dictated by internal Info-Sec controls, as well as those coming from external regulatory mandates.
For enterprises looking out for new cloud applications, I think one needs to look deeper and go beyond ‘checking the box’, which is typically done by looking at Compliance Standards around SOC2 controls, PCI-DSS, HIPAA, etc. This deeper insight can be gathered by looking at few key areas as follows:
- Underlying cloud infrastructure approach – Is it multi-tenant or multi-instance? I believe a multi-instance strategy that ensures there is no co-mingling of data across customers in the back end provides a sounds foundation for security because of the physical segregation that it leads to. There are other benefits in terms of performance and SLAs, as well.
- Encryption with key management should rest with the enterprise and not the cloud provider. This capability provides the necessary foundation for ensuring that you and the enterprise can decide where and how to provide encryption, and align it to your business needs. This will help you stay independent of your cloud provider.
- Look for how user entitlement is managed. Cloud applications need to have a sophisticated org-role construct for the segregation of duty. Often, cloud applications have only a role-based primitive to decide what a user can do in the application. However in real life, people change roles, sometimes people have to do multiple things, and as such applications that support more sophisticated models (such as a Federated Org-Role-User Mapping) are able to ensure they not only address such real life scenarios in a robust manner but in addition they are able to effectively maintain segregation of duty.
- Cloud Vendors that implement automated scans and audits around the full stack go a long way in providing security assurance. This should include hardware vulnerability management, OS patching, and application penetration testing, to application segregation-of-duty testing. In short, it should be an automated machinery that keeps a constant vigil and enforces periodic remediation.
- Finally, not all cloud application vendors will disclose their software development practices, but it is worthwhile to look at those and ask pointed questions to ensure OWASP standards, security testing (ideally by an external third party), and other Secure Software Development Life Cycle approaches are followed.
I am not prescribing that all the above 5 should be met, but the above vectors should be used to arrive at an assessment. Based on that assessment appropriate security controls can be implemented to get the full business benefit of a cloud application.











