Threat and Vulnerability Management
Measure Your Program Outcomes

- 38%
reduction in the cost of managing vulnerabilities and their impact

- 30%
reduction in the number of person-days required for scaling up the level of vulnerability management
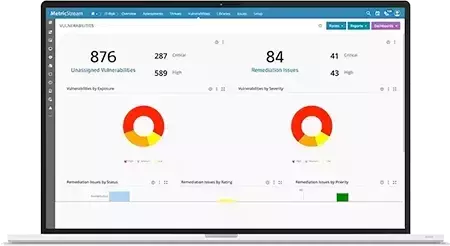
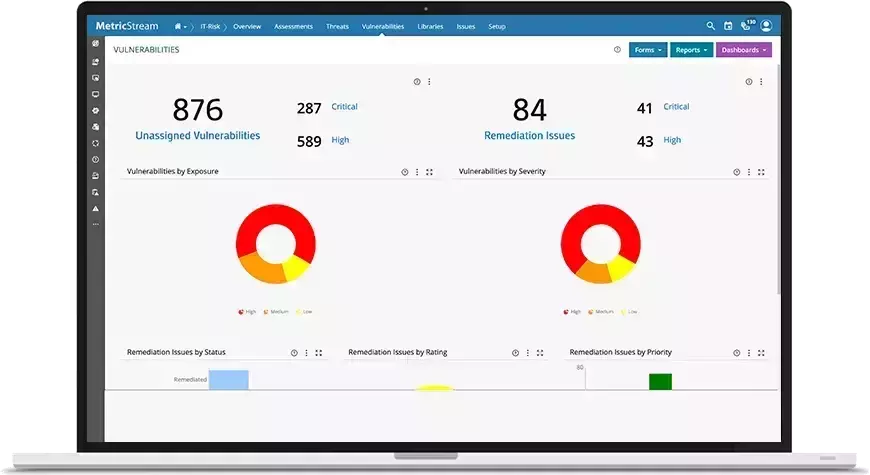
Consolidate Threat and Vulnerability Intelligence for Effective Decision-Making
MetricStream Threat and Vulnerability Management, built on the MetricStream Platform, empowers organizations to aggregate, prioritize, track, and remediate cyber risk and information security threats and vulnerabilities in an efficient, collaborative manner. Integration capabilities import and consolidate threat and vulnerability information from various sources, providing a unified view of the data availability of combined risk ratings for business assets by combining the vulnerability severity with the asset criticality rating.
How Our Threat and Vulnerability Management Software Helps You

Manage IT Assets in Business Context
Create, document, and manage IT assets, asset classes, areas of compliance, and criticality ratings in a central library by integrating with Configuration Management Databases (CMDBs). Map IT assets and business entities to the associated cyber threats and vulnerabilities. Manage and view the relationships between these data elements easily using the data browser or data explorer.
Prioritize Better with Combined Cyber Risk Ratings
Configure risk-rating rules to combine the assets’ business criticality and their vulnerabilities’ severity. Generate a Combined Risk Rating, providing a rich business and vulnerability context for vulnerability prioritization. Based on the combined risk rating, prioritize and trigger vulnerability remediation strategies.
Intelligent Issue and Remediation
Simplify issue identification and recommend issue classification based on relation by leveraging AI/ML capabilities. Define remediation rules to trigger automated remediation processes through the workflow engine.
Threat and Vulnerability Reporting
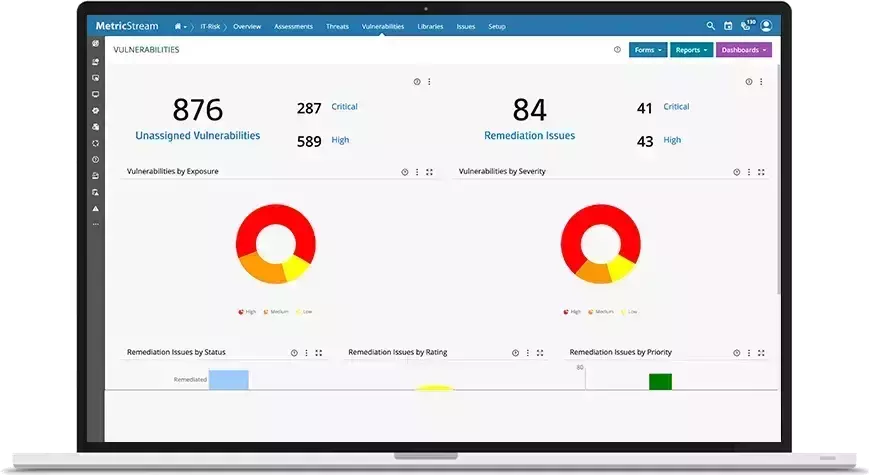
Aggregate data on threats and vulnerabilities and generate real-time intelligence, along with historical trends and statistics. Gain enterprise-wide visibility into threat and vulnerability management by leveraging executive dashboards and risk heat maps that highlight high-priority issues.
How Our Threat and Vulnerability Management Benefits Your Business
- Establish a robust and automated approach to cyber and information security threat and vulnerability management based on industry standards, best practices, and technology
- Accelerate decision-making with actionable intelligence on threats and vulnerabilities
- Improve cyber risk preparedness through an aggregated view of vulnerabilities across systems
- Stay ahead of threats and vulnerabilities with early warning notifications and proactive remediation mechanisms
Frequently Asked Questions
Yes. A built-in integration engine imports and consolidates threat and vulnerability information from various sources, thereby providing a unified view of the data. In addition, a centralized repository helps map threat and vulnerability data to assets and other business entities, enabling you to clearly visualize your information security program library (assets, asset classes, areas of compliance, and their relationships).
You can explore MetricStream CyberGRC products that enable organizations to implement a robust IT and Cyber Risk and Compliance Framework based on established security standards and industry best practices. To request a demo, click here.
Visit our Learn section to dive deeper into the GRC universe and the Insights section to explore our customer stories, webinars, thought leadership, and more.