INTRODUCTION
In today's digital age, cyber governance, risk, and compliance (Cyber GRC) programs have become critical considerations for organizations of all sizes. Cyber attacks have increased manifold in sophistication, severity, and frequency, posing a significant threat to businesses, governments, and individuals worldwide. At the same time, a deluge of new, overlapping, and occasionally differing IT and cyber laws, regulations, standards, and frameworks have made compliance activities further complex and demanding areas of organizational risk.
It is important to look at Cyber GRC holistically, not in isolation, to truly understand its interconnectedness and impact. Organizations of all sizes must take measures to protect their networks, systems, and data from cyber threats all while ensuring compliance. However, all organizations might not be equipped to do so efficiently or even equally. This is where Cyber GRC Maturity levels come into play.
"Cyber GRC Maturity" refers to an organization's ability to protect itself against cyber risks, respond effectively to attacks, stay on top of regulatory changes and requirements, and adapt to the changes in the digital landscape. It is a measure of cyber resilience – how effectively an organization can manage its cyber risk and compliance processes across the extended enterprise and prepare for, respond to, and recover from cyber incidents. It requires ongoing effort and investment to upgrade the Cyber GRC program and processes to achieve cyber resilience over time.
In this eBook, we will explore the different stages of the cyber GRC maturity journey and the characteristics of organizations at each level. The eBook will help CISOs/CSOs and security managers to evaluate which stage they are at and understand how they can move up the maturity curve
The Cyber GRC Maturity Journey
Due to the traditional on-premise deployment model of earlier IT infrastructure, a large number of organizations still have a narrow and siloed approach to managing IT and cyber risk and compliance processes. This is demonstrated aptly in the findings of the OCEG GRC Readiness for Rapid Change Survey 2022, sponsored by MetricStream, where nearly 25% of respondents said that they still use siloed, spreadsheet-based technologies, more than 15% had no standard structure, and 9% had disconnected systems.
However, given the unprecedented pace at which the cyber risk and regulatory landscape is evolving, relying on such an approach will adversely affect an organization’s ability to manage its cyber risk and compliance posture. Hence, the need to embark on the Cyber GRC maturity journey.
On the Cyber GRC maturity journey, organizations need to undertake various process, functional, and strategic level changes to enhance the efficiencies in managing IT and cyber risk, compliance, and governance activities. These changes, along with the deployment of integrated and tech-driven software solutions, help them move from the early stages involving manual and siloed processes to managing risk, embracing risk, and ultimately thriving on risk.
The generally observable stages to level up in the Cyber GRC Maturity journey are: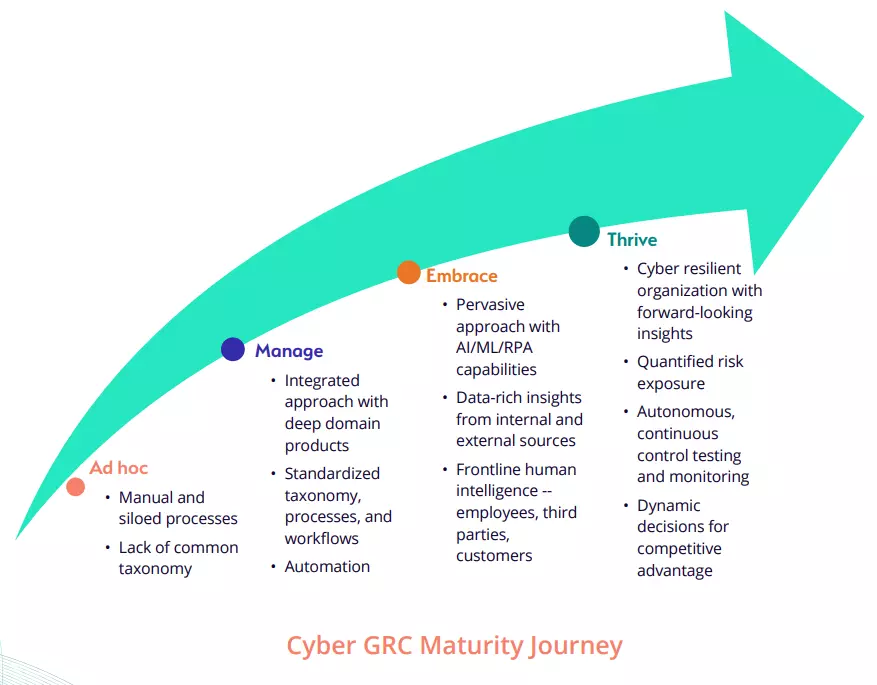
Understanding CyberGRC Maturity Levels
To embark on the Cyber GRC Maturity journey and become cyber resilient, it is important to evaluate and understand where the organization currently is. This provides required insights to proactively identify the gaps and implement measures to address them. The maturity assessment provides the CISOs and security teams with a strategic direction for optimizing the processes and strengthening the ability to protect IT and cyber infrastructure while ensuring compliance – and moving up the maturity curve.
But how does one assess which stage they are at? Here’s a complete checklist of the main features of each stage that can help you understand and evaluate your maturity level.
Ad hoc
Organizations in this stage heavily rely on manual and siloed processes, such as spreadsheets, with no standardized processes and taxonomy. There is a lot of duplication of efforts with different business units working on the same task without any collaboration or coordination. In addition to frustrating (and avoidable) errors, this results in a “reactive” approach to cyber GRC – organizations typically only respond to cyber incidents after they have occurred and often find themselves struggling to stay on top of regulatory changes. The primary reason for this is the lack of a well-defined and documented cyber GRC strategy or plan and the absence of appropriate systems and processes in place required to ensure visibility into cyber risks and compliance processes to drive better-informed decisions. Instead, organizations in this stage often resort to near-sighted firefighting until the crisis is responded to or has severely affected their continuity abilities

Manage Risk
Organizations making the move to this stage typically create and implement deep-domain products for IT and cyber risk and compliance management, IT policy management, and IT vendor management on an integrated platform with a common taxonomy. It not only helps to automate the processes, but also aids in aggregating risk information to provide detailed reports, dashboards, and insights, all of which lead to improved risk and compliance management processes.

Embrace Risk
n this stage of the journey, organizations adopt a more pervasive approach to managing Cyber GRC activities. Building upon the standardized processes and automation in the Manage level, they leverage contextual data from internal and external sources as well as advanced technologies such as artificial intelligence (AI), machine learning (ML), and robotic process automation (RPA) for IT and cyber risk and compliance management, IT policy management, and IT vendor management on an integrated platform. This, along with tapping into frontline intelligence, helps not only manage and mitigate risks across the whole enterprise but also detect lurking risks when they are observed. The entire organization embraces risk through improved visibility and collaborative actions.

Thrive on Risk
In this stage, organizations are mature enough to drive dynamic, risk-based “strategic” cyber GRC decisions. A truly resilient organization that builds upon the Embrace level and leverages quantitative assessments, AI/ML capabilities, autonomous tools, and technologies to make smarter, dynamic, and faster business decisions based on cyber GRC insights.

Organizations at the Ad hoc level are highly vulnerable to cyber risks and are likely to fall short of complying with regulatory requirements. Those at the Manage level have taken the first steps towards Cyber GRC Maturity but still have room for improvement. Organizations at the Embrace level have achieved a high degree of cyber resilience but should continue to monitor emerging risks and threats and refine their cyber GRC strategies. Organizations at the Thrive level are leaders in cyber GRC and serve as trailblazers for other organizations
In today's digital age, cyber governance, risk, and compliance (Cyber GRC) programs have become critical considerations for organizations of all sizes. Cyber attacks have increased manifold in sophistication, severity, and frequency, posing a significant threat to businesses, governments, and individuals worldwide. At the same time, a deluge of new, overlapping, and occasionally differing IT and cyber laws, regulations, standards, and frameworks have made compliance activities further complex and demanding areas of organizational risk.
It is important to look at Cyber GRC holistically, not in isolation, to truly understand its interconnectedness and impact. Organizations of all sizes must take measures to protect their networks, systems, and data from cyber threats all while ensuring compliance. However, all organizations might not be equipped to do so efficiently or even equally. This is where Cyber GRC Maturity levels come into play.
"Cyber GRC Maturity" refers to an organization's ability to protect itself against cyber risks, respond effectively to attacks, stay on top of regulatory changes and requirements, and adapt to the changes in the digital landscape. It is a measure of cyber resilience – how effectively an organization can manage its cyber risk and compliance processes across the extended enterprise and prepare for, respond to, and recover from cyber incidents. It requires ongoing effort and investment to upgrade the Cyber GRC program and processes to achieve cyber resilience over time.
In this eBook, we will explore the different stages of the cyber GRC maturity journey and the characteristics of organizations at each level. The eBook will help CISOs/CSOs and security managers to evaluate which stage they are at and understand how they can move up the maturity curve
Due to the traditional on-premise deployment model of earlier IT infrastructure, a large number of organizations still have a narrow and siloed approach to managing IT and cyber risk and compliance processes. This is demonstrated aptly in the findings of the OCEG GRC Readiness for Rapid Change Survey 2022, sponsored by MetricStream, where nearly 25% of respondents said that they still use siloed, spreadsheet-based technologies, more than 15% had no standard structure, and 9% had disconnected systems.
However, given the unprecedented pace at which the cyber risk and regulatory landscape is evolving, relying on such an approach will adversely affect an organization’s ability to manage its cyber risk and compliance posture. Hence, the need to embark on the Cyber GRC maturity journey.
On the Cyber GRC maturity journey, organizations need to undertake various process, functional, and strategic level changes to enhance the efficiencies in managing IT and cyber risk, compliance, and governance activities. These changes, along with the deployment of integrated and tech-driven software solutions, help them move from the early stages involving manual and siloed processes to managing risk, embracing risk, and ultimately thriving on risk.
The generally observable stages to level up in the Cyber GRC Maturity journey are:
To embark on the Cyber GRC Maturity journey and become cyber resilient, it is important to evaluate and understand where the organization currently is. This provides required insights to proactively identify the gaps and implement measures to address them. The maturity assessment provides the CISOs and security teams with a strategic direction for optimizing the processes and strengthening the ability to protect IT and cyber infrastructure while ensuring compliance – and moving up the maturity curve.
But how does one assess which stage they are at? Here’s a complete checklist of the main features of each stage that can help you understand and evaluate your maturity level.
Organizations in this stage heavily rely on manual and siloed processes, such as spreadsheets, with no standardized processes and taxonomy. There is a lot of duplication of efforts with different business units working on the same task without any collaboration or coordination. In addition to frustrating (and avoidable) errors, this results in a “reactive” approach to cyber GRC – organizations typically only respond to cyber incidents after they have occurred and often find themselves struggling to stay on top of regulatory changes. The primary reason for this is the lack of a well-defined and documented cyber GRC strategy or plan and the absence of appropriate systems and processes in place required to ensure visibility into cyber risks and compliance processes to drive better-informed decisions. Instead, organizations in this stage often resort to near-sighted firefighting until the crisis is responded to or has severely affected their continuity abilities

Organizations making the move to this stage typically create and implement deep-domain products for IT and cyber risk and compliance management, IT policy management, and IT vendor management on an integrated platform with a common taxonomy. It not only helps to automate the processes, but also aids in aggregating risk information to provide detailed reports, dashboards, and insights, all of which lead to improved risk and compliance management processes.

n this stage of the journey, organizations adopt a more pervasive approach to managing Cyber GRC activities. Building upon the standardized processes and automation in the Manage level, they leverage contextual data from internal and external sources as well as advanced technologies such as artificial intelligence (AI), machine learning (ML), and robotic process automation (RPA) for IT and cyber risk and compliance management, IT policy management, and IT vendor management on an integrated platform. This, along with tapping into frontline intelligence, helps not only manage and mitigate risks across the whole enterprise but also detect lurking risks when they are observed. The entire organization embraces risk through improved visibility and collaborative actions.

In this stage, organizations are mature enough to drive dynamic, risk-based “strategic” cyber GRC decisions. A truly resilient organization that builds upon the Embrace level and leverages quantitative assessments, AI/ML capabilities, autonomous tools, and technologies to make smarter, dynamic, and faster business decisions based on cyber GRC insights.

Organizations at the Ad hoc level are highly vulnerable to cyber risks and are likely to fall short of complying with regulatory requirements. Those at the Manage level have taken the first steps towards Cyber GRC Maturity but still have room for improvement. Organizations at the Embrace level have achieved a high degree of cyber resilience but should continue to monitor emerging risks and threats and refine their cyber GRC strategies. Organizations at the Thrive level are leaders in cyber GRC and serve as trailblazers for other organizations








