Introduction
The Health Insurance Portability and Accountability Act (HIPAA) plays a critical role in safeguarding sensitive patient information in the United States. In an era where healthcare organizations increasingly rely on digital solutions, protecting patient data from unauthorized access has never been more important. On December 27, 2024, the HHS Office for Civil Rights proposed additional measures to enhance cybersecurity in healthcare under HIPAA due to the growing number of cyberattacks. One of the foundational tools in this effort is the HIPAA risk assessment - a mandatory process for covered entities and business associates under the HIPAA security rule.
This blog explores the intricacies of HIPAA risk assessments, including their purpose, importance, and execution, along with practical guidance on overcoming common challenges.
Key Takeaways
- HIPAA risk assessments are systematic processes to identify potential risks to the confidentiality, integrity, and availability of electronically protected health information (ePHI).
- HIPAA risk assessments help organizations comply with federal regulations, prevent data breaches, and mitigate security vulnerabilities.
- Regular assessments build patient trust, reduce liability, and protect organizational reputation.
- The process involves identifying assets, evaluating threats, and implementing strategies to mitigate risks.
- Organizations often struggle with resource limitations, lack of expertise, and evolving cybersecurity threats.
- A robust HIPAA security risk assessment checklist can streamline the process and ensure compliance.
What is a HIPAA Risk Assessment?
A HIPAA risk assessment is a systematic evaluation conducted by healthcare organizations and their business associates to identify and mitigate risks to the security of ePHI. Required under the HIPAA security rule, the risk assessment examines physical, technical, and administrative safeguards to ensure compliance with HIPAA regulations.
It focuses on vulnerabilities in the organization’s systems and processes that could expose ePHI to unauthorized access, loss, or destruction.
What is the Purpose of a HIPAA Risk Assessment?
The goal of a HIPAA risk assessment is to safeguard patient data by identifying vulnerabilities, ensuring regulatory compliance, enhancing breach preparedness, and fostering trust through robust data protection practices.
Specifically, the process serves the following purposes:
- Regulatory Compliance: Ensures adherence to HIPAA's administrative, physical, and technical safeguard requirements.
- Data Protection: Reduces the risk of breaches and unauthorized disclosures. Incident Preparedness: Enhances the organization's ability to respond to data breaches or cybersecurity threats.
- Liability Mitigation: Protects organizations from penalties and fines resulting from non-compliance or data breaches.
- Trust Building: Demonstrates commitment to patient privacy, fostering trust among stakeholders.
Key Importance of HIPAA Risk Assessments
- Compliance with Legal Requirements Failure to perform a HIPAA risk assessment can result in substantial penalties. According to the Office for Civil Rights (OCR), the fines for non-compliance can range from $100 to $50,000 per violation, depending on the severity and the organization’s efforts to correct the issue.
- Proactive Risk Management HIPAA risk assessments enable organizations to proactively address vulnerabilities before they lead to breaches, saving costs associated with incident response and recovery.
- Enhanced Security Posture Regular assessments ensure that the organization stays ahead of evolving cyber threats and employs up-to-date security measures.
- Reputation Management Healthcare organizations that fail to safeguard patient data risk significant reputational damage, leading to a loss of trust and business opportunities.
- Support for Organizational Growth A strong data security framework established through risk assessments ensures that the organization can scale its operations without jeopardizing compliance or data security.
Who Should Perform HIPAA Security Risk Assessments?
The responsibility for conducting HIPAA security risk assessments typically falls on:
- Healthcare Providers: Includes hospitals, clinics, private practices, and long-term care facilities.
- Business Associates: Organizations that handle ePHI on behalf of covered entities, such as billing services, IT providers, and data storage companies.
- Dedicated Compliance Teams: Internal staff or external consultants with expertise in cybersecurity, data protection, and HIPAA regulations.
Smaller organizations may lack the resources or expertise to perform assessments in-house, making third-party consultants a viable option.
Common Challenges When Conducting HIPAA Security Assessments
Here are some obstacles organizations might face while conducting HIPAA security assessments:
- Resource Constraints Smaller organizations often struggle with limited budgets and personnel to dedicate to comprehensive risk assessments.
- Complex Regulatory Landscape The intricate requirements of HIPAA can be overwhelming, especially for organizations new to compliance.
- Evolving Cybersecurity Threats As cyber threats grow in sophistication, organizations face the challenge of keeping their security measures up to date.
- Lack of Expertise Many organizations lack in-house expertise in cybersecurity or compliance, leading to gaps in the assessment process.
- Data Silos Disparate systems and a lack of centralized data management can hinder the effectiveness of risk assessments.
How to Conduct a HIPAA Security Risk Assessment
Conducting a HIPAA risk assessment includes the following requirements:
Step 1: Identify Assets and Data Flows
- Document all locations where ePHI is created, received, maintained, or transmitted.
- Include physical assets (e.g., servers, workstations) and virtual environments (e.g., cloud storage).
Step 2: Evaluate Threats and Vulnerabilities
- Identify potential threats, including cyberattacks, human error, and natural disasters.
- Assess vulnerabilities in current security measures, such as outdated software or insufficient access controls.
Step 3: Analyze Potential Impact
- Determine the potential impact of a breach or data loss, including financial, legal, and reputational consequences.
Step 4: Develop Risk Mitigation Strategies
- Implement technical safeguards (e.g., encryption, firewalls) and administrative controls (e.g., training, policies).
- Address high-priority risks first while planning for long-term improvements.
Step 5: Document Findings and Actions
- Maintain comprehensive documentation of the assessment process, findings, and mitigation efforts.This documentation is critical for demonstrating compliance during audits.
Step 6: Review and Update Regularly
- Conduct assessments annually or after significant organizational changes, such as adopting new technologies or experiencing a data breach.
Why Do You Need a HIPAA Security Risk Assessment Checklist?
A HIPAA security risk assessment template simplifies the assessment process by providing a structured framework for compliance. Here’s why it’s essential:
- Consistency: Ensures that no critical components are overlooked during the assessment.
- Efficiency: Streamlines the process, saving time and resources.
- Accountability: Assigns responsibilities for specific tasks, reducing the risk of errors.
- Compliance Proof: Serves as evidence of due diligence in case of an OCR audit.
- Training Tool: Helps educate staff on key compliance areas.
Key Elements of a Checklist:
- Identification of ePHI locations and data flows.
- Assessment of administrative, physical, and technical safeguards.
- Documentation of identified risks and mitigation measures.
- Regular review and updates to reflect changing regulatory requirements.
How Does MetricStream Help with HIPAA Compliance?
MetricStream provides a comprehensive framework to help organizations streamline and automate all aspects of HIPAA compliance. Organizations can effectively break down restrictive silos to become more collaborative and integrated. They are equipped to streamline all aspects of HIPAA compliance such as preparing policies and procedures, assessing and analyzing risks, managing audits, identifying gaps and remedying issues. Powerful capabilities like built-in remediation workflows, time tracking, e-mail based notifications, and risk monitoring improve operational efficiency and effectiveness. In addition, automated controls reduce the time and effort required for HIPAA compliance.
Here's how MetricStream helps you achieve HIPAA compliance
Centralized Compliance Environment Design
MetricStream provides a centralized framework to record and maintain all patient records, policies and procedures, certificates, and other data in line with HIPAA rules. It enables organizations to establish a central repository that stores and organizes policies and procedure documents and links them with the compliance, risk, and control framework at each section and sub-section levels. For instance, the risk of unauthorized access to patient data can be immediately associated with a password encryption control.
Streamlined Policy and Document Management
Built-in tools support policy implementation, acceptance, exception tracking, and mapping of policies to compliance requirements. Powerful analytics and reporting with graphical dashboards help track each policy from origin to obsolescence, giving managers complete visibility into the system. Integrated collaboration and workflow tools can be used to access, create, modify, review, and approve policy and procedure documents in a systematic manner. They help to accelerate the review and approval process by automatically moving documents from one stage to the next
Efficient Risk and Control Assessment
Based on configurable methodologies and algorithms, MetricStream helps organizations effectively identify, assess, and prioritize risks. Configurable risk calculators and risk heat maps help monitor organizational risk profile and report risk activities and results. Organizations can leverage embedded control frameworks such as COSO and ISO 27002 to define a set of controls that can then be used to mitigate risks. Powerful testing capabilities enable assessment and monitoring the effectiveness of controls.
Robust Reporting Capabilities
MetricStream automatically tracks and routes the flow of information to help managers assess the effectiveness of internal controls, adherence to policies, and overall risk profile. It provides the flexibility to create and maintain pre-defined reports as well as ad hoc or scheduled reports. Graphical dashboards provide complete, real-time visibility into enterprise-wide HIPAA compliance processes and statuses. They display statistics and data according to policy type, risk status, audit history, and in-process documents. They can also be drilled down to view data at a finer level of detail
Systematic Management of Certifications and Attestations
Well-defined workflows enable managing certifications in a consistent, reliable and predictable manner. MetricStream helps enforce accountability by facilitating the flow of information and records and documenting attestations and representations at appropriate stages. Organizations can configure and execute certifications and self-assessments by leveraging predefined templates and schedules for designated executives. Support for electronic sign-offs at departmental and functional levels roll up for executive certifications. MetricStream also supports procedures for affirming the strength of internal controls and adherence to policies. This information rolls up to executive managers who can review and certify the overall risk and control assessment for the enterprise in conformance with HIPAA requirements.
AI-Powered Issue management and Remediation
MetricStream provides powerful capabilities to improve responsiveness to issues identified. Built-in artificial intelligence capabilities enable effortless classification of issues based on relationships, criticality, and business impact. It helps to accelerate the process of creating and implementing remediation plans and routing to reviewers for approval with real-time tracking of issue remediation.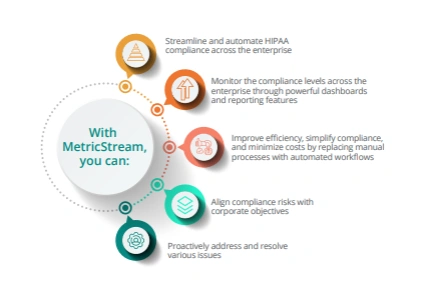
To request a personalized demo, click here
Why MetricStream
A HIPAA security risk assessment is not just a regulatory requirement — it’s a strategic tool for safeguarding sensitive patient information and ensuring organizational resilience. By understanding its purpose, importance, and challenges, healthcare organizations can create robust processes to protect ePHI. Whether performed internally or with the help of experts, regular assessments empower organizations to stay compliant, build trust, and thrive in an increasingly digital landscape.
For organizations seeking to simplify the process, adopting a HIPAA security risk assessment checklist demonstrates their commitment to patient privacy, regulatory compliance, and operational excellence. With MetricStream’s comprehensive CyberGRC solutions, organizations can meet HIPAA compliance requirements more effectively and efficiently. To know more, request a personalized demo.
Frequently Asked Questions (FAQ)
How often should a HIPAA risk assessment be conducted?
HIPAA risk assessments should be conducted annually or whenever significant changes occur in the organization.
What type of questions are required in a HIPAA risk assessment?
Questions about data locations, potential threats, vulnerabilities, and existing safeguards are required in a HIPAA risk assessment.
What tools or frameworks can be used for a HIPAA risk assessment?
For HIPAA risk assessment, tools like NIST Cybersecurity Framework, HHS Security Risk Assessment Tool, or third-party risk assessment software.
The Health Insurance Portability and Accountability Act (HIPAA) plays a critical role in safeguarding sensitive patient information in the United States. In an era where healthcare organizations increasingly rely on digital solutions, protecting patient data from unauthorized access has never been more important. On December 27, 2024, the HHS Office for Civil Rights proposed additional measures to enhance cybersecurity in healthcare under HIPAA due to the growing number of cyberattacks. One of the foundational tools in this effort is the HIPAA risk assessment - a mandatory process for covered entities and business associates under the HIPAA security rule.
This blog explores the intricacies of HIPAA risk assessments, including their purpose, importance, and execution, along with practical guidance on overcoming common challenges.
- HIPAA risk assessments are systematic processes to identify potential risks to the confidentiality, integrity, and availability of electronically protected health information (ePHI).
- HIPAA risk assessments help organizations comply with federal regulations, prevent data breaches, and mitigate security vulnerabilities.
- Regular assessments build patient trust, reduce liability, and protect organizational reputation.
- The process involves identifying assets, evaluating threats, and implementing strategies to mitigate risks.
- Organizations often struggle with resource limitations, lack of expertise, and evolving cybersecurity threats.
- A robust HIPAA security risk assessment checklist can streamline the process and ensure compliance.
A HIPAA risk assessment is a systematic evaluation conducted by healthcare organizations and their business associates to identify and mitigate risks to the security of ePHI. Required under the HIPAA security rule, the risk assessment examines physical, technical, and administrative safeguards to ensure compliance with HIPAA regulations.
It focuses on vulnerabilities in the organization’s systems and processes that could expose ePHI to unauthorized access, loss, or destruction.
The goal of a HIPAA risk assessment is to safeguard patient data by identifying vulnerabilities, ensuring regulatory compliance, enhancing breach preparedness, and fostering trust through robust data protection practices.
Specifically, the process serves the following purposes:
- Regulatory Compliance: Ensures adherence to HIPAA's administrative, physical, and technical safeguard requirements.
- Data Protection: Reduces the risk of breaches and unauthorized disclosures. Incident Preparedness: Enhances the organization's ability to respond to data breaches or cybersecurity threats.
- Liability Mitigation: Protects organizations from penalties and fines resulting from non-compliance or data breaches.
- Trust Building: Demonstrates commitment to patient privacy, fostering trust among stakeholders.
- Compliance with Legal Requirements Failure to perform a HIPAA risk assessment can result in substantial penalties. According to the Office for Civil Rights (OCR), the fines for non-compliance can range from $100 to $50,000 per violation, depending on the severity and the organization’s efforts to correct the issue.
- Proactive Risk Management HIPAA risk assessments enable organizations to proactively address vulnerabilities before they lead to breaches, saving costs associated with incident response and recovery.
- Enhanced Security Posture Regular assessments ensure that the organization stays ahead of evolving cyber threats and employs up-to-date security measures.
- Reputation Management Healthcare organizations that fail to safeguard patient data risk significant reputational damage, leading to a loss of trust and business opportunities.
- Support for Organizational Growth A strong data security framework established through risk assessments ensures that the organization can scale its operations without jeopardizing compliance or data security.
The responsibility for conducting HIPAA security risk assessments typically falls on:
- Healthcare Providers: Includes hospitals, clinics, private practices, and long-term care facilities.
- Business Associates: Organizations that handle ePHI on behalf of covered entities, such as billing services, IT providers, and data storage companies.
- Dedicated Compliance Teams: Internal staff or external consultants with expertise in cybersecurity, data protection, and HIPAA regulations.
Smaller organizations may lack the resources or expertise to perform assessments in-house, making third-party consultants a viable option.
Here are some obstacles organizations might face while conducting HIPAA security assessments:
- Resource Constraints Smaller organizations often struggle with limited budgets and personnel to dedicate to comprehensive risk assessments.
- Complex Regulatory Landscape The intricate requirements of HIPAA can be overwhelming, especially for organizations new to compliance.
- Evolving Cybersecurity Threats As cyber threats grow in sophistication, organizations face the challenge of keeping their security measures up to date.
- Lack of Expertise Many organizations lack in-house expertise in cybersecurity or compliance, leading to gaps in the assessment process.
- Data Silos Disparate systems and a lack of centralized data management can hinder the effectiveness of risk assessments.
Conducting a HIPAA risk assessment includes the following requirements:
Step 1: Identify Assets and Data Flows
- Document all locations where ePHI is created, received, maintained, or transmitted.
- Include physical assets (e.g., servers, workstations) and virtual environments (e.g., cloud storage).
Step 2: Evaluate Threats and Vulnerabilities
- Identify potential threats, including cyberattacks, human error, and natural disasters.
- Assess vulnerabilities in current security measures, such as outdated software or insufficient access controls.
Step 3: Analyze Potential Impact
- Determine the potential impact of a breach or data loss, including financial, legal, and reputational consequences.
Step 4: Develop Risk Mitigation Strategies
- Implement technical safeguards (e.g., encryption, firewalls) and administrative controls (e.g., training, policies).
- Address high-priority risks first while planning for long-term improvements.
Step 5: Document Findings and Actions
- Maintain comprehensive documentation of the assessment process, findings, and mitigation efforts.This documentation is critical for demonstrating compliance during audits.
Step 6: Review and Update Regularly
- Conduct assessments annually or after significant organizational changes, such as adopting new technologies or experiencing a data breach.
A HIPAA security risk assessment template simplifies the assessment process by providing a structured framework for compliance. Here’s why it’s essential:
- Consistency: Ensures that no critical components are overlooked during the assessment.
- Efficiency: Streamlines the process, saving time and resources.
- Accountability: Assigns responsibilities for specific tasks, reducing the risk of errors.
- Compliance Proof: Serves as evidence of due diligence in case of an OCR audit.
- Training Tool: Helps educate staff on key compliance areas.
Key Elements of a Checklist:
- Identification of ePHI locations and data flows.
- Assessment of administrative, physical, and technical safeguards.
- Documentation of identified risks and mitigation measures.
- Regular review and updates to reflect changing regulatory requirements.
MetricStream provides a comprehensive framework to help organizations streamline and automate all aspects of HIPAA compliance. Organizations can effectively break down restrictive silos to become more collaborative and integrated. They are equipped to streamline all aspects of HIPAA compliance such as preparing policies and procedures, assessing and analyzing risks, managing audits, identifying gaps and remedying issues. Powerful capabilities like built-in remediation workflows, time tracking, e-mail based notifications, and risk monitoring improve operational efficiency and effectiveness. In addition, automated controls reduce the time and effort required for HIPAA compliance.
Here's how MetricStream helps you achieve HIPAA compliance
Centralized Compliance Environment Design
MetricStream provides a centralized framework to record and maintain all patient records, policies and procedures, certificates, and other data in line with HIPAA rules. It enables organizations to establish a central repository that stores and organizes policies and procedure documents and links them with the compliance, risk, and control framework at each section and sub-section levels. For instance, the risk of unauthorized access to patient data can be immediately associated with a password encryption control.
Streamlined Policy and Document Management
Built-in tools support policy implementation, acceptance, exception tracking, and mapping of policies to compliance requirements. Powerful analytics and reporting with graphical dashboards help track each policy from origin to obsolescence, giving managers complete visibility into the system. Integrated collaboration and workflow tools can be used to access, create, modify, review, and approve policy and procedure documents in a systematic manner. They help to accelerate the review and approval process by automatically moving documents from one stage to the next
Efficient Risk and Control Assessment
Based on configurable methodologies and algorithms, MetricStream helps organizations effectively identify, assess, and prioritize risks. Configurable risk calculators and risk heat maps help monitor organizational risk profile and report risk activities and results. Organizations can leverage embedded control frameworks such as COSO and ISO 27002 to define a set of controls that can then be used to mitigate risks. Powerful testing capabilities enable assessment and monitoring the effectiveness of controls.
Robust Reporting Capabilities
MetricStream automatically tracks and routes the flow of information to help managers assess the effectiveness of internal controls, adherence to policies, and overall risk profile. It provides the flexibility to create and maintain pre-defined reports as well as ad hoc or scheduled reports. Graphical dashboards provide complete, real-time visibility into enterprise-wide HIPAA compliance processes and statuses. They display statistics and data according to policy type, risk status, audit history, and in-process documents. They can also be drilled down to view data at a finer level of detail
Systematic Management of Certifications and Attestations
Well-defined workflows enable managing certifications in a consistent, reliable and predictable manner. MetricStream helps enforce accountability by facilitating the flow of information and records and documenting attestations and representations at appropriate stages. Organizations can configure and execute certifications and self-assessments by leveraging predefined templates and schedules for designated executives. Support for electronic sign-offs at departmental and functional levels roll up for executive certifications. MetricStream also supports procedures for affirming the strength of internal controls and adherence to policies. This information rolls up to executive managers who can review and certify the overall risk and control assessment for the enterprise in conformance with HIPAA requirements.
AI-Powered Issue management and Remediation
MetricStream provides powerful capabilities to improve responsiveness to issues identified. Built-in artificial intelligence capabilities enable effortless classification of issues based on relationships, criticality, and business impact. It helps to accelerate the process of creating and implementing remediation plans and routing to reviewers for approval with real-time tracking of issue remediation.
To request a personalized demo, click here
A HIPAA security risk assessment is not just a regulatory requirement — it’s a strategic tool for safeguarding sensitive patient information and ensuring organizational resilience. By understanding its purpose, importance, and challenges, healthcare organizations can create robust processes to protect ePHI. Whether performed internally or with the help of experts, regular assessments empower organizations to stay compliant, build trust, and thrive in an increasingly digital landscape.
For organizations seeking to simplify the process, adopting a HIPAA security risk assessment checklist demonstrates their commitment to patient privacy, regulatory compliance, and operational excellence. With MetricStream’s comprehensive CyberGRC solutions, organizations can meet HIPAA compliance requirements more effectively and efficiently. To know more, request a personalized demo.
How often should a HIPAA risk assessment be conducted?
HIPAA risk assessments should be conducted annually or whenever significant changes occur in the organization.
What type of questions are required in a HIPAA risk assessment?
Questions about data locations, potential threats, vulnerabilities, and existing safeguards are required in a HIPAA risk assessment.
What tools or frameworks can be used for a HIPAA risk assessment?
For HIPAA risk assessment, tools like NIST Cybersecurity Framework, HHS Security Risk Assessment Tool, or third-party risk assessment software.








